We are creative, ambitious and ready for challenges! Hire Us
Smart Street Light Poles Control Application
- Introduction
- Project Name: Smart Street Light Poles Control Application
- Category: Web & Mobile Application
- Published: June, 2022
A Smart Light Pole by most definitions is a light pole that has intelligent Lighting. Smart street lighting has already replaced the traditional street lights in many smart cities around the globe. The smart pole offers current mobile network providers a solution for increased difficulty to acquire access in congested areas as the conventional poles are unable to swith on or offd light status.
- What you need to know about this application development?
- Mobile Application ~ To develop mobile application for Smart pole controle we used Flutter. Flutter is an open-source UI software development kit created by Google. It is used to develop cross platform applications for Android, iOS, Linux, macOS, Windows, Google Fuchsia, and the web from a single cose.
- Web Application ~ We used LARAVEL and Mysql, Laravel php framework to create this Web application it is an incredibly powerful tool for web development. Bootstrap, it’s potent front-end css framework used to create modern websites and It’s open-source and free to use, yet features numerous HTML and CSS templates for UI interface elements such as buttons and forms. Bootstrap also supports JavaScript extensions.
- Key Smart Street Light Poles Control Application Features
The Key Smart Street Light Poles Control Application is a versatile and comprehensive solution designed to facilitate the management of smart street lighting systems through both web and mobile platforms. This integrated system allows city officials, maintenance teams, and operators to monitor, control, and optimize street lighting for safety, efficiency, and sustainability.
Web Application
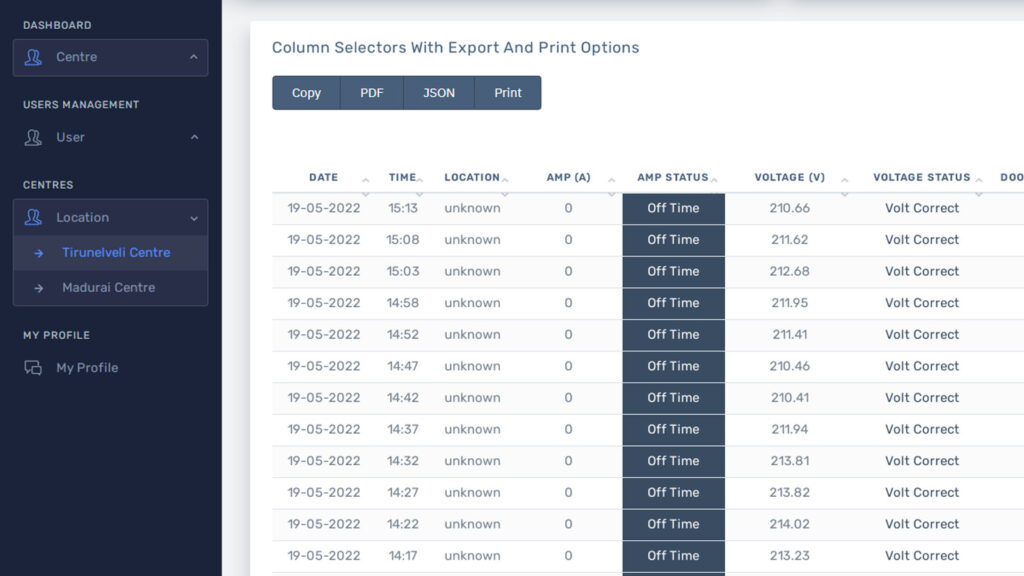
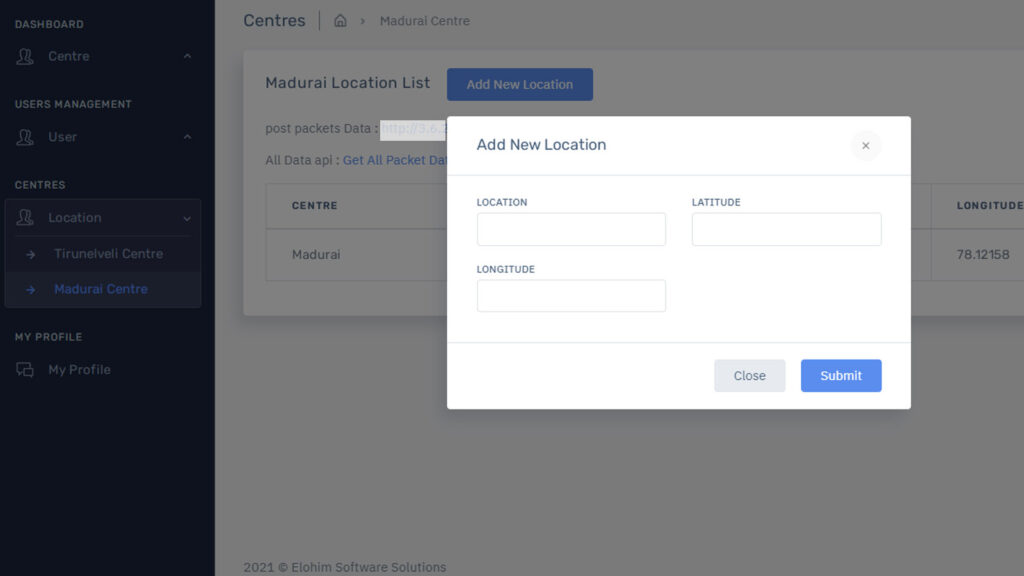
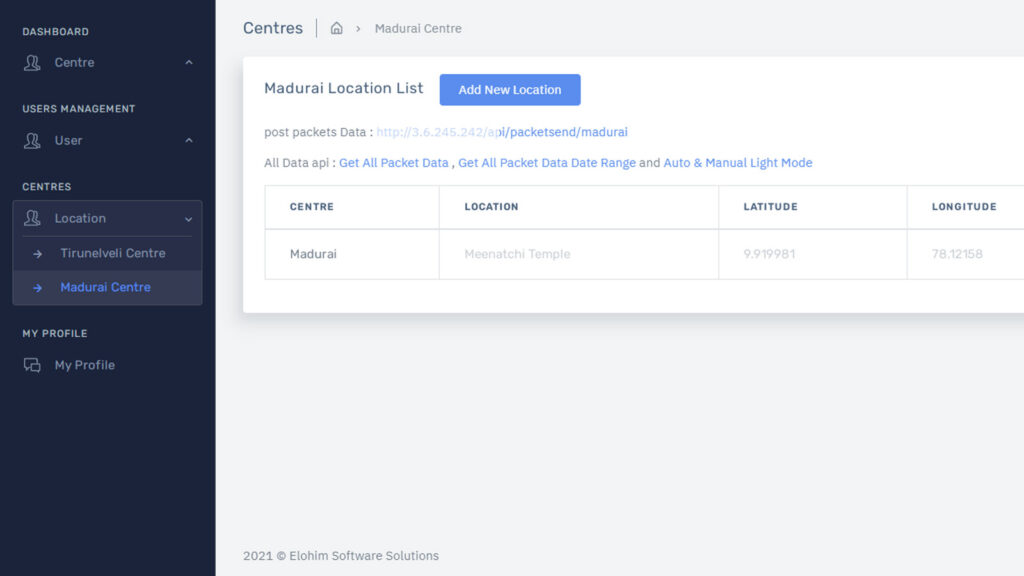
The Key Smart Street Light Poles Control Web Application is a comprehensive tool for managing smart pole lighting systems. It offers real-time monitoring and control features that ensure the efficient and safe operation of street lighting. Here are the key features:
- Status Monitoring
- Voltage Alerts
- Voltage and Amp Monitoring
- Neutral and Short Circuit Detection
- Fault Detection and Maintenance Alerts
Mobile Application
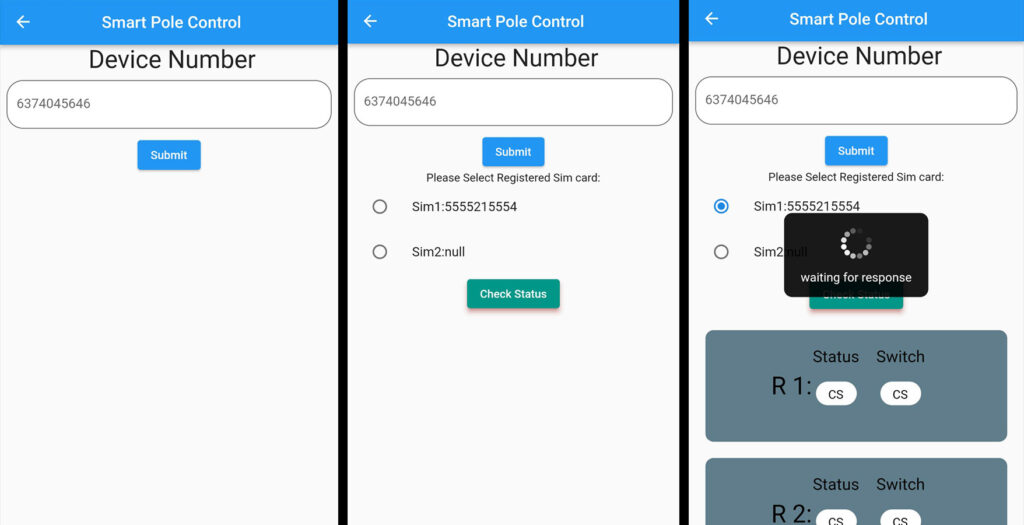
The Key Smart Street Light Poles Control Mobile Application provides convenient features for controlling smart pole lights directly from a mobile device. Here are the primary features:
- Remote On/Off Control
- Real-Time Status Monitoring
- Group Control
- Scheduling & Automation
- Alerts and Notifications
- Related Projects